Another day, another report of Android malware wreaking havoc across the world. Earlier this month, security researchers from Check Point published a report on a newly discovered piece of malware called HummingBad that has reportedly infected as many as 10 million devices worldwide.
According to the report, the malware is being run by a Chinese group called YingMob which leverages the malware to install fraudulent apps and generate fraudulent ad revenue. “The group is highly organized,” Check Point notes, “with 25 employees that staff four separate groups responsible for developing HummingBad’s malicious components.” What’s more, the group appears to be extremely successful, with revenue from their malicious undertaking reportedly bringing in as much as $300,000 per month. As it stands now, most affected devices happen to be located in China and in India..
As for how the malware operates and manages to gain access to a particular device, the report notes that HummingBad began as a “drive-by download attack” wherein the malware was pushed down to a device when users visited malicious sites, often adult-oriented websites.
HummingBad uses a sophisticated, multi-stage attack chain with two main components. The first component attempts to gain root access on a device with a rootkit that exploits multiple vulnerabilities. If successful, attackers gain full access to a device. If rooting fails, a second component uses a fake system update notification, tricking users into granting HummingBad system-level permissions.
Irrespective of whether rooting is successful, HummingBad downloads as many fraudulent apps to the device as possible. The malicious apps in the HummingBad campaign are made of a mix of several malicious components, many of which have variations with the same functionality. In some cases, the malicious components are dynamically downloaded onto a device after the infected app is installed.
When installed, the malware results in ad banners popping on user devices with a “close” button that in reality registers as a click on the ad in question. Notably, the appearance of an ad banner cannot be dismissed until a click is registered.
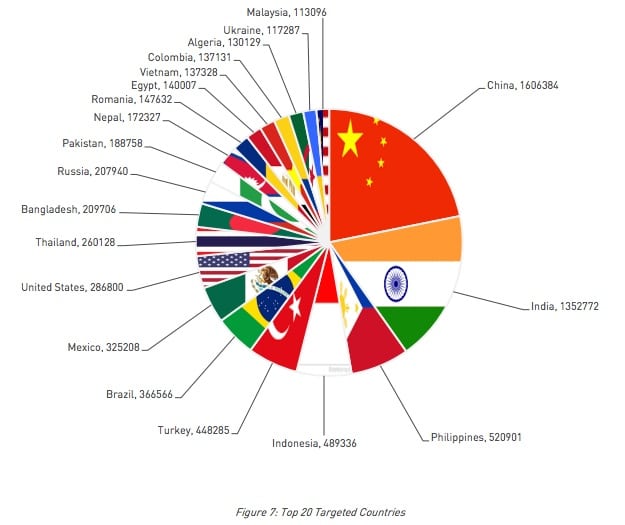
The distribution of the malware worldwide can be seen below.
As for a breakdown across varying versions of Android, KitKat users are the most widely affected.
Source :BGR
BREAKING NEWS | HEADLINE NEWS | NEWS | DAILY NEWS | WEEKLY NEWS
WORLD NEWS | INDONESIA NEWS | BALI NEWS

















Add a comment